Intercept HTTPS Network Traffic from WatchOS 11
This mini-blog would demonstrate how to intercept network Traffic from the WatchOS app (Update with WatchOS 11 and Xcode 16).
1. WatchOS Sample app
Fortunately, from WatchOS 11, it's straightforward to intercept HTTP/HTTPS network traffic from your WatchOS applications by using Proxyman app.
To get started, let download a WatchOS example app, which is already integrated with an Alamofire Framework.
Then, open the watchOS Example.xcodeproj project with Xcode. At this time, it's Xcode 16.
2. Create a new WatchOS 11 Simulator and pair with iOS Simulator
It's important to create a new WatchOS 11 Simulator and pair with iOS Simulator, so Proxyman can capture the traffic from the WatchOS app.
2.1 Open Xcode -> Device Menu -> Devices & Simulators
- Click on the "+" button on the top left corner
- Select "Apple Watch Series 10"
- Click on "Create"
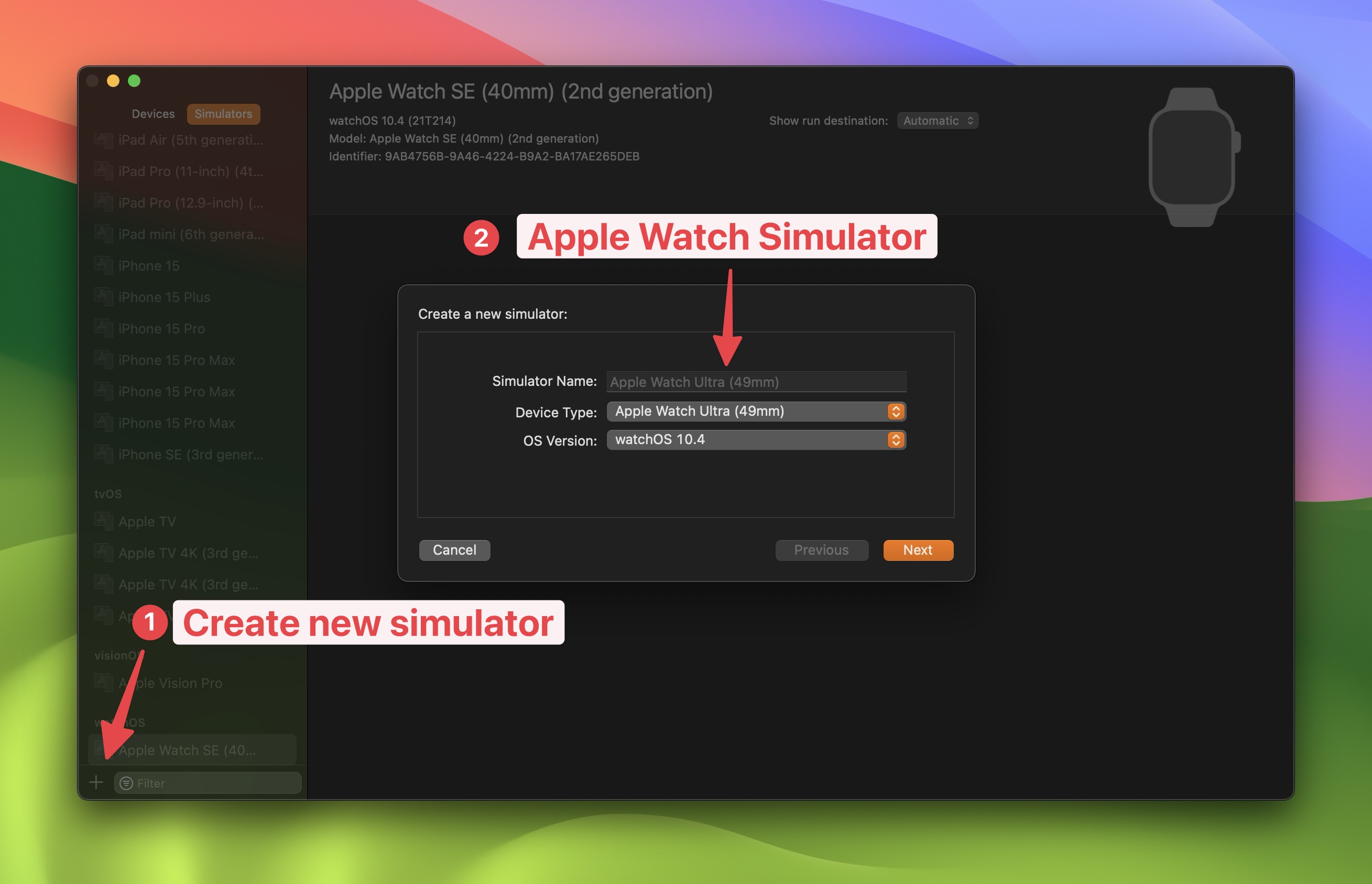
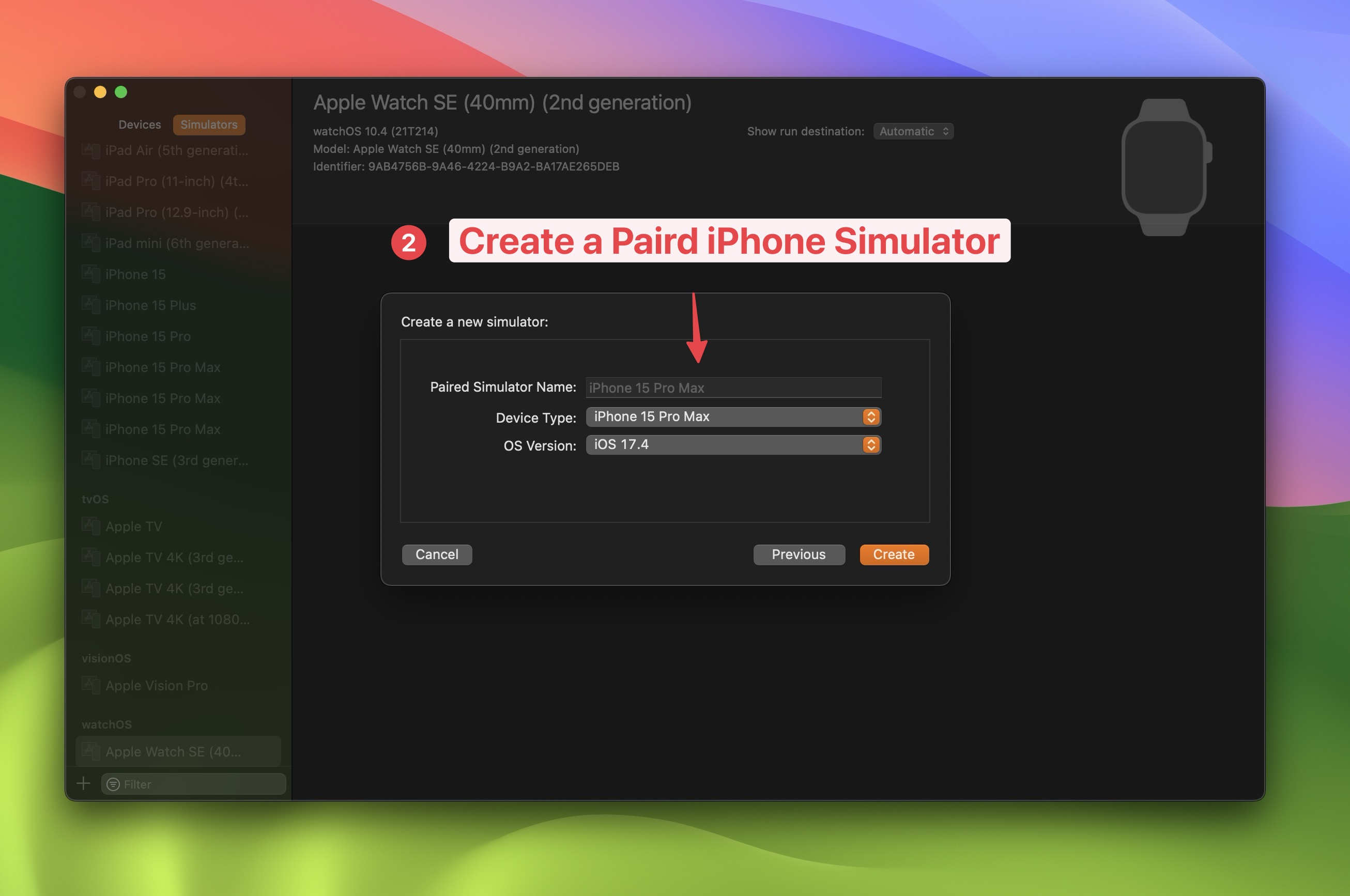
- Create a paired iOS Simulator
2.3 Back to Xcode, select Watch OS Example WatchKit app target -> Apple Watch Series 11.
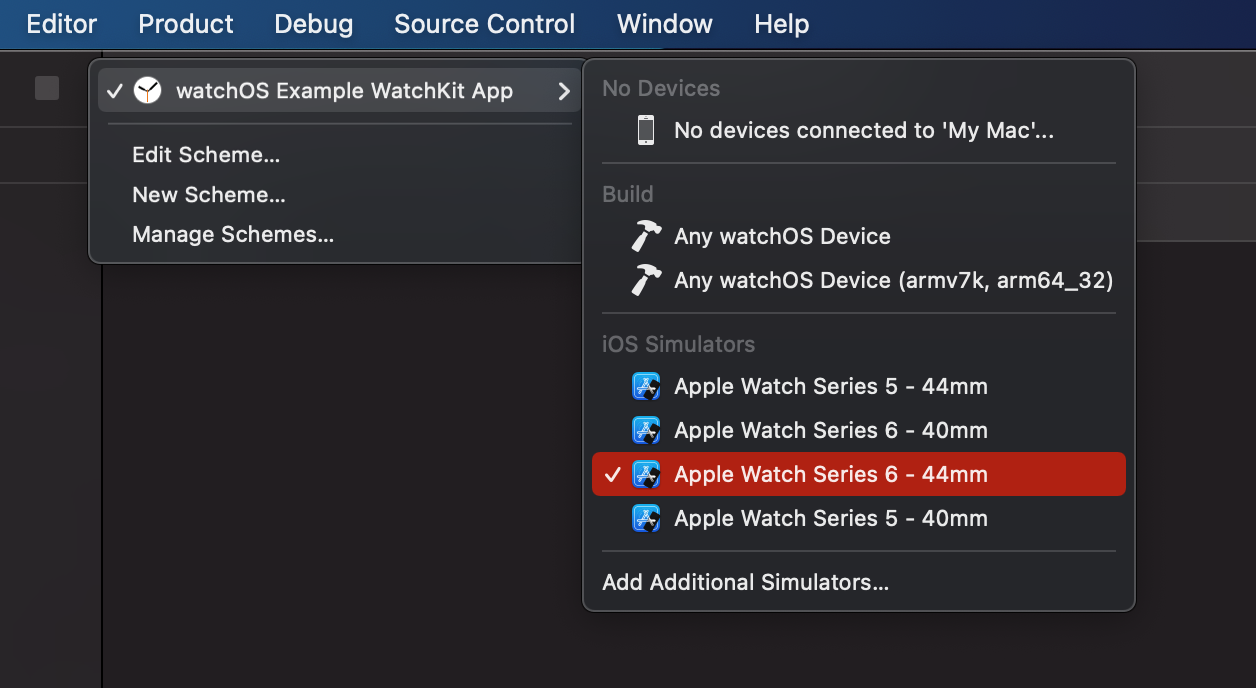
Then, starting the app.
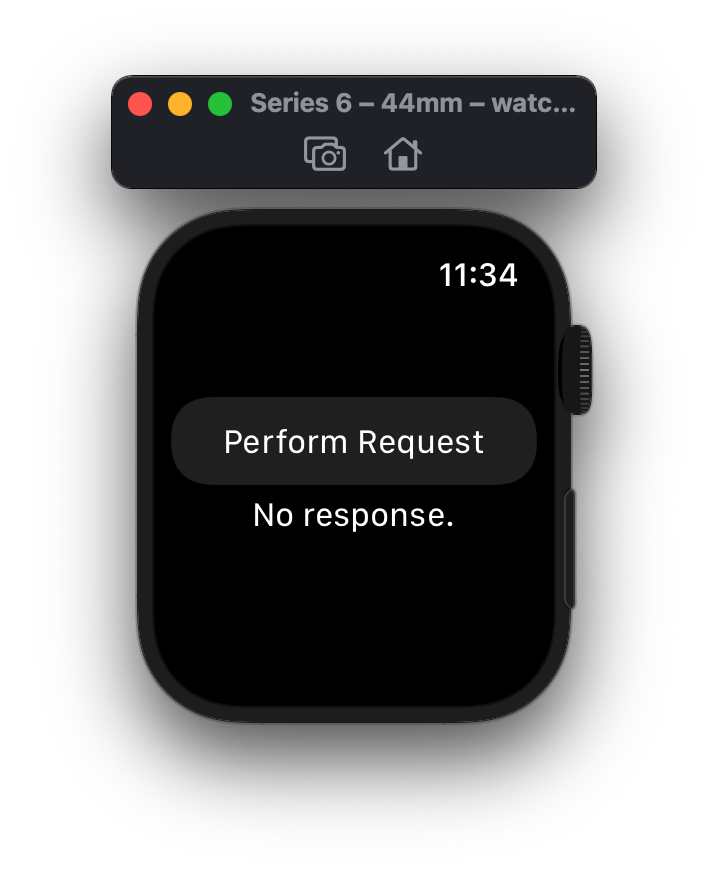
As soon as you click the "Perform Request" button, it will make a GET Request to the httpbin.org server.
2. Intercept with Proxyman
Let open Proxyman app and install the certificate to Watch OS Simulator.
Please navigate to Certificate menu -> Install Certificate for iOS -> Simulator.
Then following all steps and make sure they are all ticked.
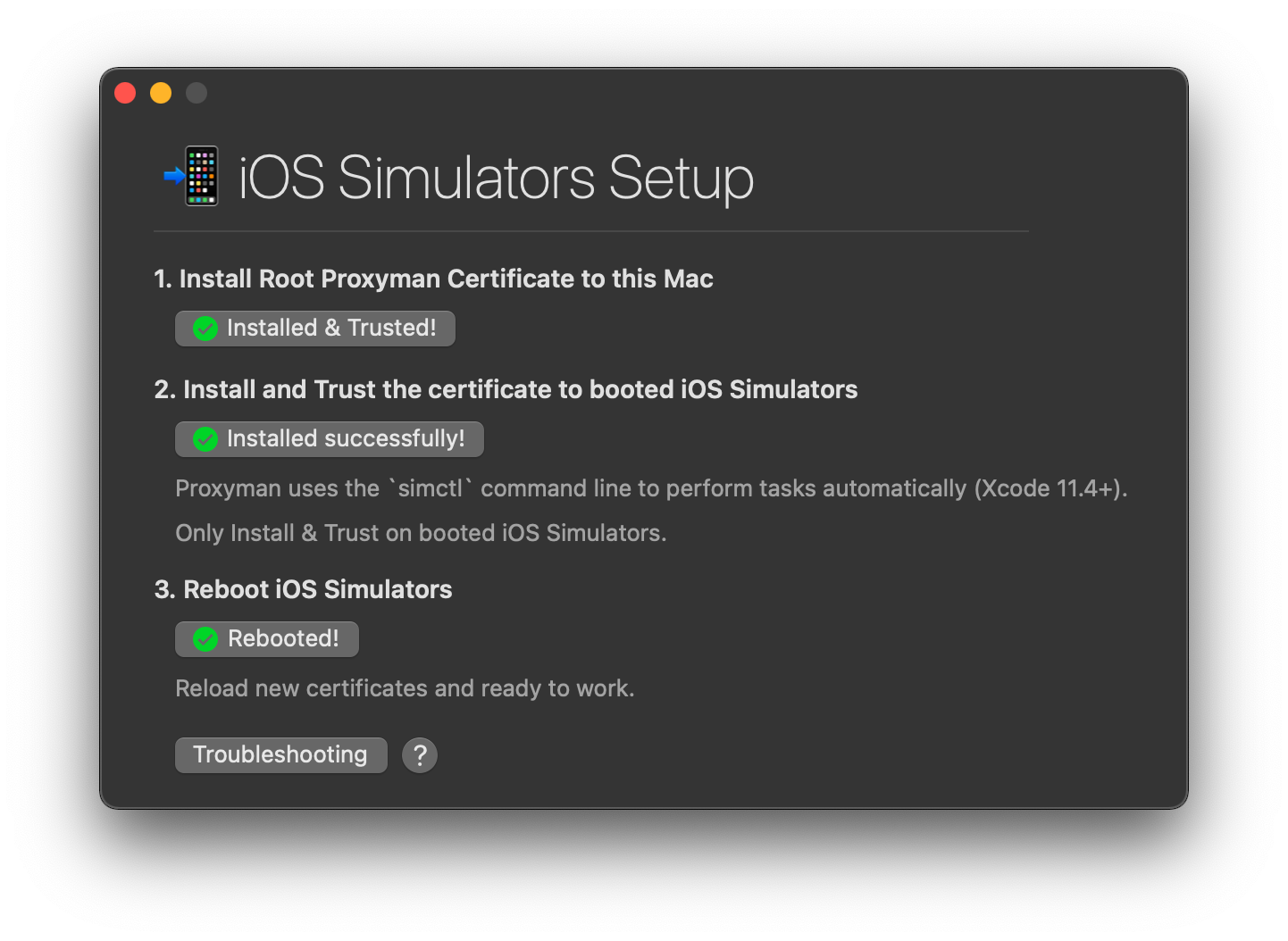
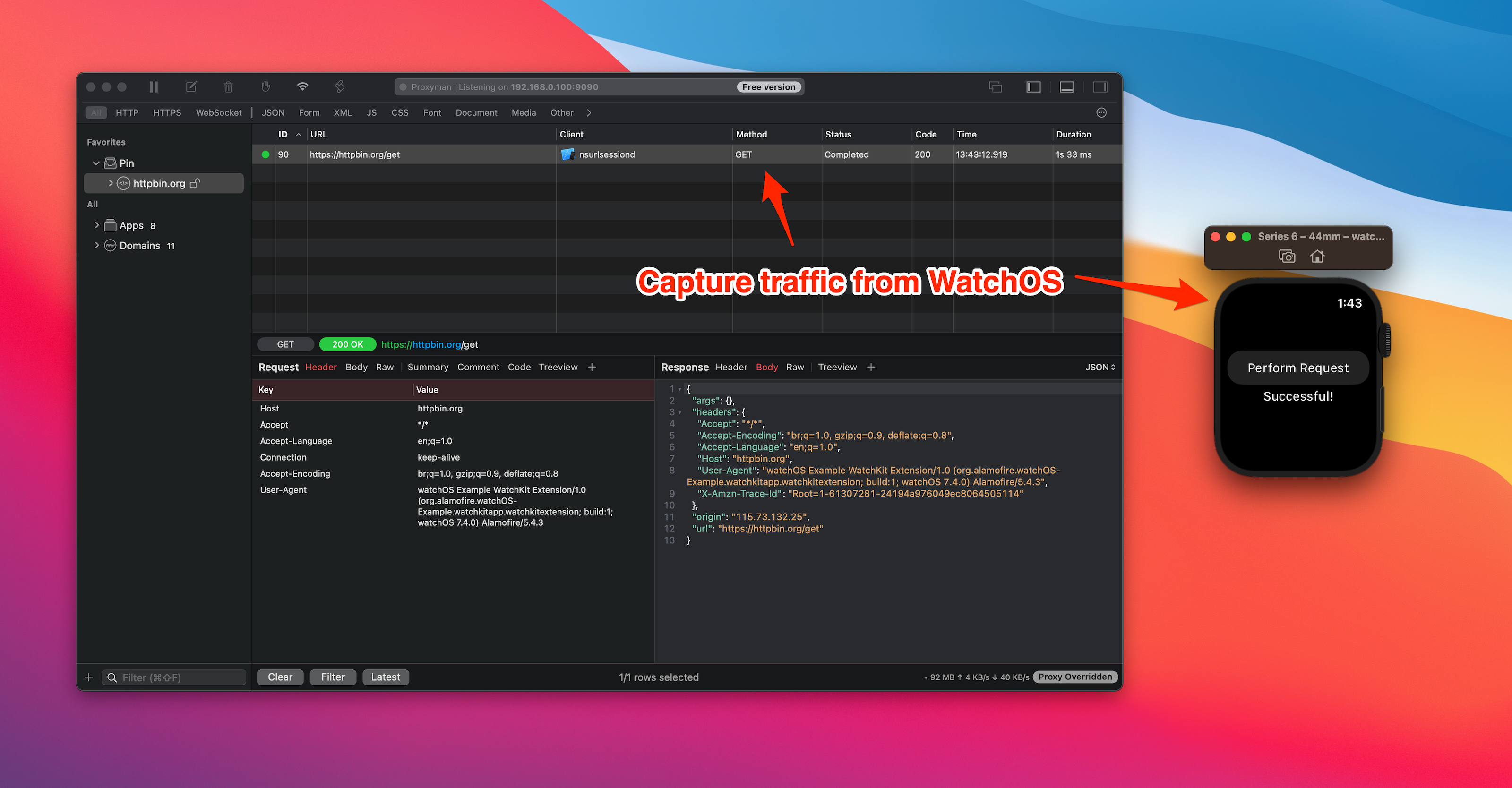
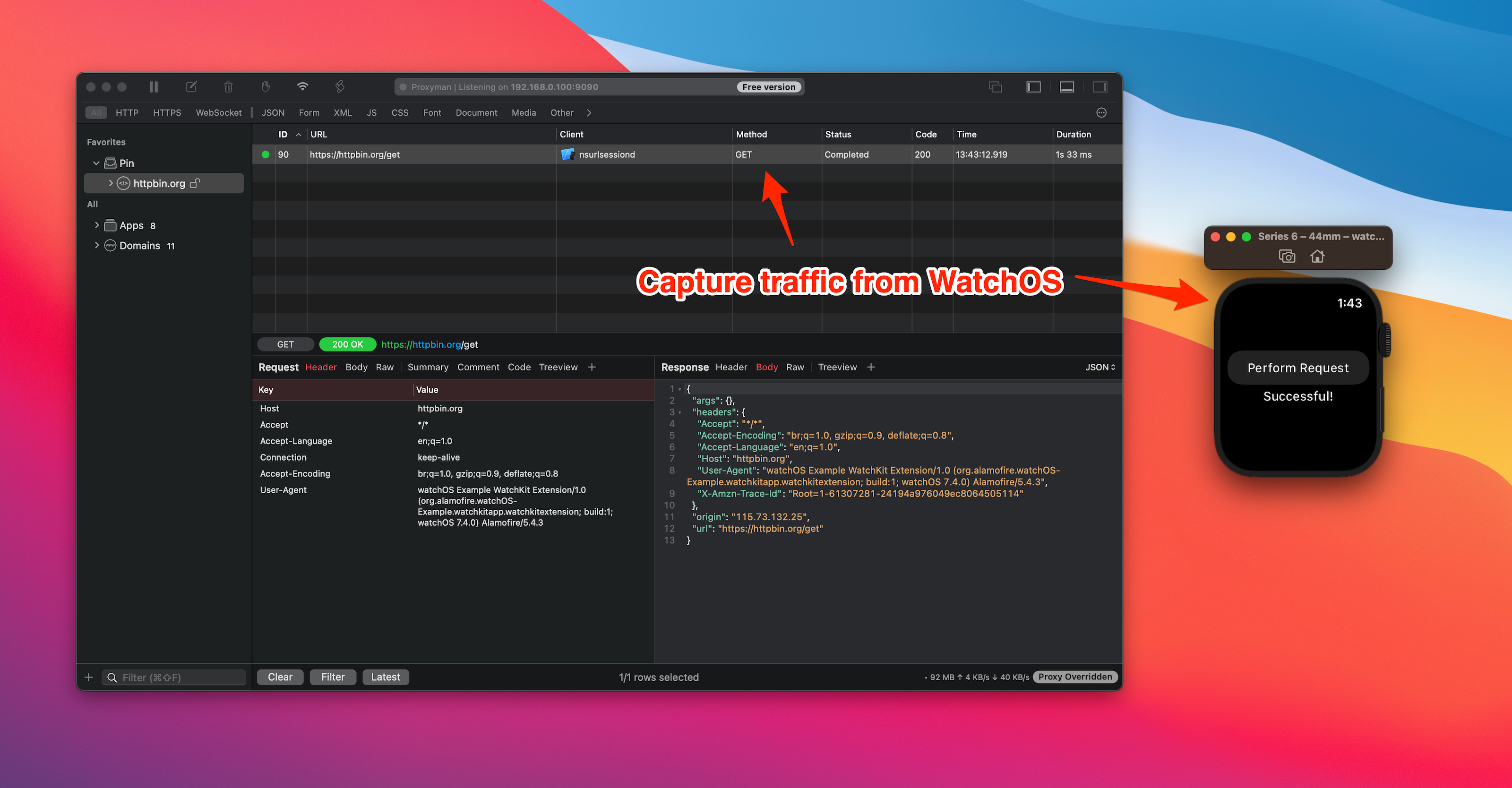
It's ready to intercept traffic with Proxyman. Let click on the "Perform Request" button on the Watch OS.
Tada! You can see the new request/response in Proxyman.
3. What's next
To capture traffic from a physical WatchOS device, it's a little tricky. You have to install and trust the certificate on your host iOS Devices and set up WatchOS to proxy traffic to the iOS device. We will write a tutorial on how to achieve it in the next blog.
Proxyman is a high-performance macOS app, which enables developers to capture HTTPs traffic on iOS device, iOS Simulator and Android devices.
Get it at https://proxyman.io